By Syed Jawad Imam Jafri, Cyber Security and Privacy Officer (CSPO), Huawei South Africa – Huawei’s 5G cyber security follows the design principles of defense in depth, Zero-trust@5G, and adaptive security, which collaboratively provide a systematic, dynamic, and adaptive security framework.
Defense in depth provides multi-layer security measures to protect critical internal assets from external threats. Different security technologies are used at different layers to prevent the compromise of a single point affecting the entire system. Defense in depth prevents system breakdown caused by attacks and unauthorized access.
In addition, information is encrypted, so even if it is stolen, no information leakage will occur. Moreover, malicious tampering can be identified so that mitigation measures can be taken accordingly. Zero trust is becoming a trend in cyber security. It assumes that the network is always vulnerable to risks and that no access is trusted before authentication.
Therefore, access authentication, dynamic authorization, and continuous assessment are required to implement dynamic access control. Zero trust in the telecom field, that is, Zero-trust@5G, shall be adapted based on the service characteristics of mobile communications networks to improve 5G cyber security.
Currently, Zero-trust@5G can focus on two important scenarios: O&M management and UE access. It implements dynamic and precise access control for O&M identity management and 5G UE access, to identify spoofing and prevent unauthorized access.
Through the IPDRR methodology, adaptive security enables dynamic, continuous, closed-loop optimization of security measures to adapt to ever-changing security threats, supporting rapid system recovery.
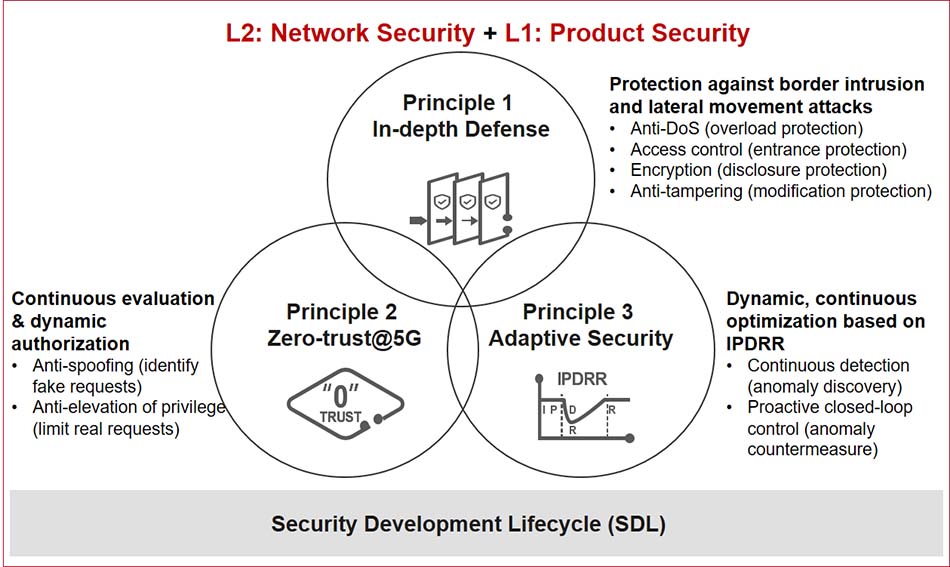
Figure 1: design principles for 5G cyber security
5G inherits security protection mechanisms in 4G, and adds data integrity protection for the user plane to prevent data tampering on the user plane. In addition, the confidentiality and integrity protection of UE capability reporting information is added in R16 to prevent UE privacy breaches or denial of service (DoS) attacks caused by UE capability eavesdropping or tampering.
In terms of transport security, the N2/N3 interfaces connecting the access and core networks and Xn interfaces connecting base stations use Internet Protocol Security (IPsec) in 4G for transport security. 5G additionally supports Datagram Transport Layer Security (DTLS) over Stream Control Transmission Protocol (SCTP) to secure signaling transmission on the control plane, ensuring transport security between RANs and core networks. Operators can select a transport security protection scheme based on security requirements to prevent data breach and tampering on the transport network.
In terms of privacy protection, 5G security standards include encryption schemes for concealing the SUPI to tackle the risk of user information leakage through messages sent for the initial UE access, thereby enhancing privacy protection.
On the basis of 5G security standards for network equipment, Huawei further provides the following air interface and system security hardening measures:
- Anti-DDoS: Base stations can identify distributed denial of service (DDoS) attacks launched at them through the air interface from malicious UEs and mitigate the attacks using specific control mechanisms, ensuring the availability of base stations.
- Rogue Base Station Detection: To prevent rogue base stations from launching spoofing attacks on base stations and UEs over the air interface, base stations provide the rogue base station detection function based on the 5G NSA/SA network architecture, helping operators identify and locate rogue base stations.
- Hardware Hardening: Hardware ports of base stations are hardened to prevent near-end attacks. Unused ports are disabled by default, and an alarm is generated upon any change in the port status, reducing the risk of near-end attacks.
- OS Hardening: OSs are hardened to prevent attacks. By default, unnecessary services are disabled on the OSs of base stations. Login from an OS user is prohibited, preventing attacks.
- Secure Boot: To prevent the system from being tampered with during boot and runtime, base stations support secure boot, detection of code segment tampering during runtime, and alarm reporting, enhancing system integrity protection.
- Base Station Encryption: To prevent sensitive data, such as keys and passwords, from being stolen or tampered with, base stations store encrypted information in chips, which cannot be obtained externally.
